Cybersecurity for Smart Home Devices
by ago0

Smart home devices are devices that can be controlled and monitored remotely through the internet. Examples of smart home devices include smart thermostats, smart lights, smart locks, and smart security cameras. These devices offer a range of benefits and conveniences, such as the ability to control the temperature of your home from your smartphone or to receive notifications when someone is at your door.
The popularity and adoption of smart home devices have grown rapidly in recent years. According to a report by Statista, the number of smart home devices in use worldwide is expected to reach 1.61 billion by 2025. This growth is driven by a number of factors, including the increasing availability of affordable smart home devices, the convenience they offer, and the growing awareness of energy savings and security.
Understanding the Cybersecurity Threats to Smart Homes
While smart home devices offer many benefits, they also present a number of cybersecurity threats. These threats include the risk of unauthorized access, data breaches, and the potential for attackers to use smart home devices to gain access to other devices on the same network.
Attackers can exploit vulnerabilities in smart home devices in a number of ways. For example, they may use malware to gain access to a device, or they may use brute force attacks to guess weak passwords. Once they have gained access, attackers can use smart home devices to spy on homeowners, steal sensitive information, or launch attacks on other devices on the network.
The potential consequences of a smart home security breach can be serious. In addition to the risk of financial loss and identity theft, a security breach can also result in the loss of privacy and the potential for physical harm. For example, an attacker could use a smart lock to gain unauthorized access to a home, or they could use a smart thermostat to create dangerous conditions inside the home.
Common Smart Home Vulnerabilities and How to Avoid Them
There are a number of common vulnerabilities in smart home devices that attackers can exploit. These vulnerabilities include the use of default passwords, outdated software, and insecure communication protocols. To avoid these vulnerabilities, it is important to take a few simple precautions when selecting and using smart home devices.
When selecting smart home devices, look for devices that have strong security features, such as encryption and two-factor authentication. It is also important to regularly check for and install security updates, as these updates often include patches for known vulnerabilities. Additionally, avoid using default passwords and instead, use strong, unique passwords for each device.
Best Practices for Securing Your Home Network
Securing your home network is an important part of protecting your smart home devices. Here are a few best practices for securing your home network:
- Change default passwords: Default passwords are often easy for attackers to guess, so it is important to change them as soon as possible.
- Enable encryption: Encryption helps to protect your network traffic from being intercepted and read by attackers.
- Use a separate network for smart home devices: This can help to isolate smart home devices from other devices on your network, making it more difficult for attackers to gain access to them.
- Keep software up-to-date: Outdated software can leave vulnerabilities that can be exploited by hackers. Setting up automatic updates or regularly checking for updates can help keep your device secure.
The Role of Manufacturers in Smart Home Cybersecurity
Manufacturers play an important role in ensuring the cybersecurity of their smart home devices. It is important for manufacturers to implement security features in their devices, such as encryption and two-factor authentication, and to regularly release security updates to patch known vulnerabilities.
Failing to prioritize cybersecurity can have serious consequences for manufacturers. In addition to the potential for financial loss and damage to their reputation, manufacturers may also face legal action and regulatory fines if their devices are found to be insecure.
Importance of Regular Software Updates and Patches
Regular software updates and patches are essential for maintaining the cybersecurity of smart home devices. These updates often include patches for known vulnerabilities, as well as new features and improvements. Failing to install updates and patches can leave devices vulnerable to attack and can also result in decreased performance and stability.
To ensure that smart home devices are always running the latest software, it is important to regularly check for and install updates. Many devices can be set to automatically install updates, which can help to ensure that they are always up-to-date.
Implementing Strong Passwords and Two-Factor Authentication
Implementing strong, unique passwords for smart home devices is an important part of protecting them from attack. A strong password should be at least 12 characters long and should include a mix of letters, numbers, and special characters. Additionally, it is important to avoid using the same password for multiple devices.
Two-factor authentication adds an extra layer of security by requiring users to provide a second form of authentication, such as a fingerprint or a code sent to their smartphone. This makes it more difficult for attackers to gain access to devices, even if they have guessed the password.
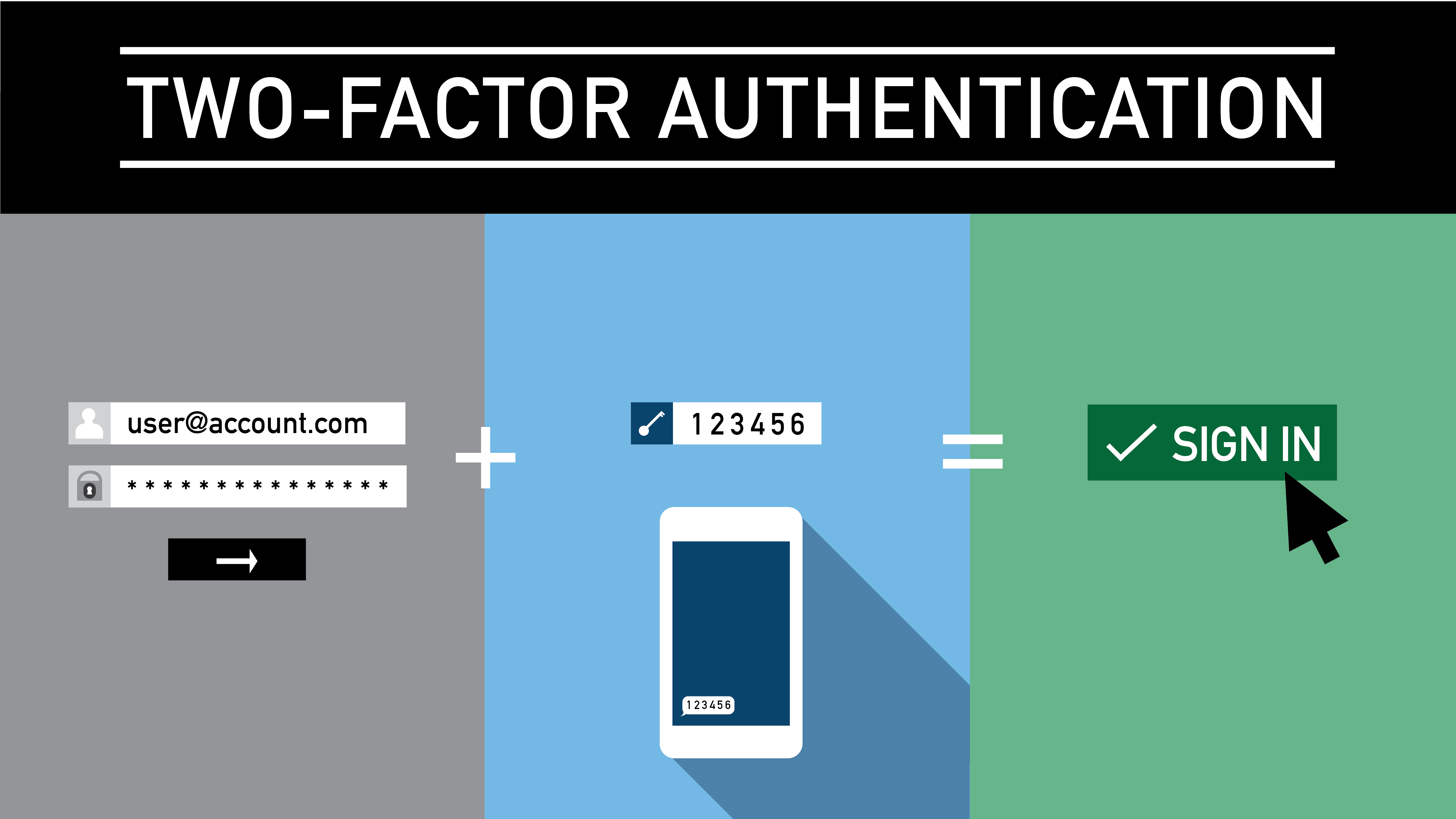
Understanding 2FA
Two-Factor Authentication (2FA), also known as Two-Step Verification, is a security process in which users provide two different authentication factors to verify themselves.
This process is designed to increase security by requiring two different types of identification. Typically, these factors fall into two categories:
- Something you know: This could be a password or a PIN.
- Something you have: This would be a physical token or a mobile device.
By requiring two different types of authentication, 2FA makes it significantly harder for attackers to gain access to a user’s accounts or systems, even if they have managed to obtain one of the authentication factors, such as a password.
Many online services, including social media platforms, banking apps, and email providers, offer 2FA as an optional or mandatory security feature. Users can usually set up 2FA in their account settings.
Securely Connecting Smart Home Devices to the Internet
Securely connecting smart home devices to the internet is an important part of protecting them from attack. Here are a few tips for securely connecting smart home devices:
- Use a virtual private network (VPN): A VPN can help to protect your network traffic from being intercepted and read by attackers.
- Disable remote access: Remote access allows devices to be accessed from anywhere, but it also increases the risk of attack. Disabling remote access can help to reduce this risk.
The Use of Encryption in Smart Home Communications
Encryption plays an important role in protecting smart home communications from attack. Encryption helps to ensure that data transmitted between devices is confidential and has not been tampered with. There are a number of different types of encryption that can be used to secure smart home communications, including symmetric and asymmetric encryption.
To ensure that smart home communications are encrypted, it is important to use devices that support encryption and to use secure communication protocols, such as HTTPS and SSH. Additionally, it is important to regularly check for and install security updates, as these updates often include patches for known vulnerabilities in encryption algorithms.
Identifying and Responding to Smart Home Security Breaches
Identifying and responding to smart home security breaches is an important part of protecting your devices and data. Here are a few signs of a security breach:
- Unusual network traffic: If you notice unusual network traffic, such as a sudden spike in data usage, it could be a sign of a security breach.
- Unauthorized access: If you notice that devices are being accessed by unauthorized users, it could be a sign of a security breach.
- Changes in device behavior: If devices are behaving unexpectedly, such as turning on or off on their own, it could be a sign of a security breach.
If you suspect that your smart home devices have been compromised, it is important to take immediate action. This may include changing passwords, disconnecting affected devices from the network, and reporting the breach to the appropriate authorities.
Legislation and Regulation in Smart Home Cybersecurity
There are a number of laws and regulations related to smart home cybersecurity. These laws and regulations vary by country and region, but they generally require manufacturers to implement certain security features in their devices and to provide regular security updates. Failure to comply with these laws and regulations can result in fines and legal action.
Additionally, there are a number of industry standards related to smart home cybersecurity. These standards, such as the Consumer Technology Association’s (CTA) Cybersecurity Certification Program, provide guidelines for manufacturers on how to design and build secure smart home devices. Compliance with these standards can help to ensure that devices are secure and can also provide a competitive advantage in the marketplace.
The Future of Cybersecurity for Smart Home Devices
The future of cybersecurity for smart home devices is likely to be shaped by a number of factors, including emerging technologies and changing user behavior. Here are a few potential developments in smart home cybersecurity:
- Artificial intelligence: Artificial intelligence (AI) can be used to detect and respond to cyber threats in real-time. AI can also be used to predict and prevent cyber attacks before they occur.
- Blockchain: Blockchain technology can be used to create secure, decentralized networks for smart home devices. This can help to reduce the risk of cyber attacks and can also provide a more secure and transparent way to manage device data.
- User education: As smart home devices become more popular, it is important for users to be educated about the cybersecurity risks and best practices. This can help to reduce the risk of user error and can also increase awareness of the importance of cybersecurity.
To stay up-to-date with smart home cybersecurity, it is important to regularly check for and install security updates, use strong, unique passwords, and follow best practices for securing your home network.
Additionally, it is important to stay informed about emerging technologies and changing user behavior, as these factors can have a significant impact on smart home cybersecurity.